Better understand your WAN with an SD-WAN Assessment
Analyse your applications, edge performance and security with no risk.
Assess your Wide Area Network
Whether an MPLS, existing SD-WAN or just an internet-based organisation, the SD-WAN assessment will assist you in evaluating or enhancing the application performance, operational efficiency and security of your WAN.
The SD-WAN assessment will allow you to gain visibility and control over applications running and potential cloud connectivity enhancements. SD-WAN also enables organisations to take advantage of the ever-changing and competitive Internet service offerings available while ensuring reliability.
Sign-up to claim free SD-WAN assessment offer
Free offer only for South Australian businesses
What will be in the detailed assessment report
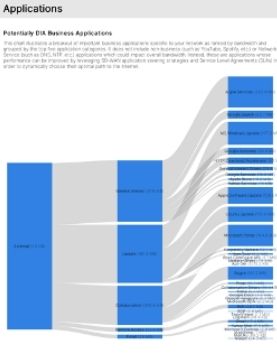
Direct Internet Access Business Application
Detailed list of all internet-based applications in use specific to your network as ranked by bandwidth and grouped by the top 5 application categories.

Top Malware and At-Risk Hosts
Known malware detected, and at-risk hosts including malicious file types - botnet C&C, virus, adware and more, the number of such files in the network, type of delivery method, and name of the malware.
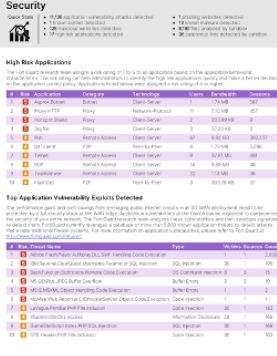
Application Risks
Detected high risk applications with a risk rating of 1 to 5 based on application behavioural characteristics. The risk rating helps network administrators to identify high risk application instantly and implement better application control policy.
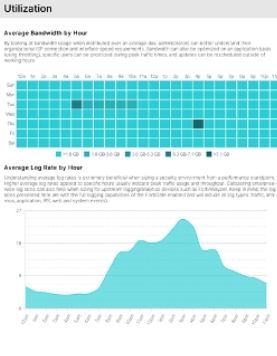
Bandwidth Consumption
Average bandwidth utilisation by time of day. Get a sharper understanding of organisational ISP connection and interface speed requirement, by looking at bandwidth usage distributed over an average day. Get a view of the average log rate to determine sizing security environment from a performance standpoint.

Top Locations
By looking at IP source traffic, know the originating country of any particular request. Certain botnets, command and control functions, and even remote access can be session heavy and indicative of targeted attacks or persistent threats from nation-states.
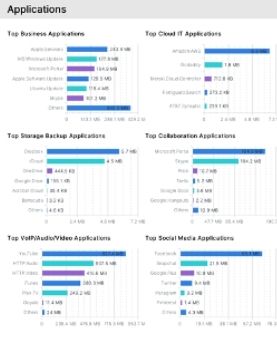
Top Applications
Top applications used, broken down by category including business applications, cloud IT applications, top storage backup applications, collaboration applications, multi-media applications like VoIP/Audio/Video applications and social media applications being assessed over the network.
How it Works
Without disrupting your existing network, we will monitor your internal traffic for a week. At the end of the collection period, we'll generate a report detailing all of the threats bypassing your existing security controls.
